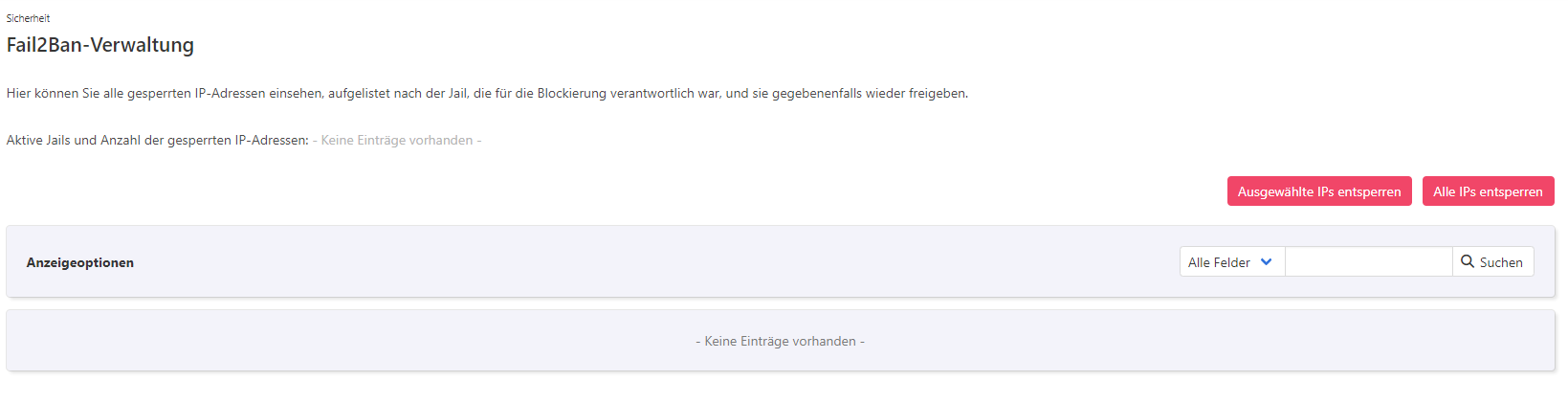
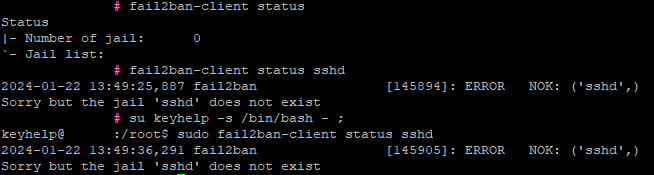
Code: Select all
2024-01-22 13:52:48,152 fail2ban.server [146293]: INFO --------------------------------------------------
2024-01-22 13:52:48,152 fail2ban.server [146293]: INFO Starting Fail2ban v0.11.2
2024-01-22 13:52:48,152 fail2ban.observer [146293]: INFO Observer start...
2024-01-22 13:52:48,154 fail2ban.database [146293]: INFO Connected to fail2ban persistent database '/var/lib/fail2ban/fail2ban.sqlite3'
2024-01-22 13:52:48,155 fail2ban.jail [146293]: INFO Creating new jail 'sshd'
2024-01-22 13:52:48,156 fail2ban.jail [146293]: ERROR Backend 'systemd' failed to initialize due to No module named 'systemd'
2024-01-22 13:52:48,156 fail2ban.jail [146293]: ERROR Failed to initialize any backend for Jail 'sshd'
2024-01-22 13:52:48,156 fail2ban.transmitter [146293]: WARNING Command ['server-stream', [['set', 'syslogsocket', 'auto'], ['set', 'loglevel', 'INFO'], ['set', 'logtarget', '/var/log/fail2ban.log'], ['set', 'dbfile', '/var/lib/fail2ban/fail2ban.sqlite3'], ['set', 'dbmaxmatches', 10], ['set', 'dbpurgeage', '1d'], ['add', 'sshd', 'systemd'], ['set', 'sshd', 'usedns', 'warn'], ['set', 'sshd', 'prefregex', '^<F-MLFID>\\s*(?:\\S+\\s+)?(?:sshd(?:\\[\\d+\\])?:?\\s+)?(?:kernel:\\s?\\[ *\\d+\\.\\d+\\]:?\\s+)?</F-MLFID>(?:(?:error|fatal): (?:PAM: )?)?<F-CONTENT>.+</F-CONTENT>$'], ['set', 'sshd', 'maxlines', 1], ['multi-set', 'sshd', 'addfailregex', ['^[aA]uthentication (?:failure|error|failed) for <F-USER>.*</F-USER> from <HOST>( via \\S+)?(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User not known to the underlying authentication module for <F-USER>.*</F-USER> from <HOST>(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^Failed publickey for invalid user <F-USER>(?P<cond_user>\\S+)|(?:(?! from ).)*?</F-USER> from <HOST>(?: (?:port \\d+|on \\S+)){0,2}(?: ssh\\d*)?(?(cond_user): |(?:(?:(?! from ).)*)$)', '^Failed (?:<F-NOFAIL>publickey</F-NOFAIL>|\\S+) for (?P<cond_inv>invalid user )?<F-USER>(?P<cond_user>\\S+)|(?(cond_inv)(?:(?! from ).)*?|[^:]+)</F-USER> from <HOST>(?: (?:port \\d+|on \\S+)){0,2}(?: ssh\\d*)?(?(cond_user): |(?:(?:(?! from ).)*)$)', '^<F-USER>ROOT</F-USER> LOGIN REFUSED FROM <HOST>', '^[iI](?:llegal|nvalid) user <F-USER>.*?</F-USER> from <HOST>(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User <F-USER>\\S+|.*?</F-USER> from <HOST> not allowed because not listed in AllowUsers(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User <F-USER>\\S+|.*?</F-USER> from <HOST> not allowed because listed in DenyUsers(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User <F-USER>\\S+|.*?</F-USER> from <HOST> not allowed because not in any group(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^refused connect from \\S+ \\(<HOST>\\)', '^Received <F-MLFFORGET>disconnect</F-MLFFORGET> from <HOST>(?: (?:port \\d+|on \\S+)){0,2}:\\s*3: .*: Auth fail(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User <F-USER>\\S+|.*?</F-USER> from <HOST> not allowed because a group is listed in DenyGroups(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', "^User <F-USER>\\S+|.*?</F-USER> from <HOST> not allowed because none of user's groups are listed in AllowGroups(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$", '^<F-NOFAIL>pam_[a-z]+\\(sshd:auth\\):\\s+authentication failure;</F-NOFAIL>(?:\\s+(?:(?:logname|e?uid|tty)=\\S*)){0,4}\\s+ruser=<F-ALT_USER>\\S*</F-ALT_USER>\\s+rhost=<HOST>(?:\\s+user=<F-USER>\\S*</F-USER>)?(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^maximum authentication attempts exceeded for <F-USER>.*</F-USER> from <HOST>(?: (?:port \\d+|on \\S+)){0,2}(?: ssh\\d*)?(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^User <F-USER>\\S+|.*?</F-USER> not allowed because account is locked(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*', '^<F-MLFFORGET>Disconnecting</F-MLFFORGET>(?: from)?(?: (?:invalid|authenticating)) user <F-USER>\\S+</F-USER> <HOST>(?: (?:port \\d+|on \\S+)){0,2}:\\s*Change of username or service not allowed:\\s*.*\\[preauth\\]\\s*$', '^Disconnecting: Too many authentication failures(?: for <F-USER>\\S+|.*?</F-USER>)?(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*$', '^<F-NOFAIL>Received <F-MLFFORGET>disconnect</F-MLFFORGET></F-NOFAIL> from <HOST>(?: (?:port \\d+|on \\S+)){0,2}:\\s*11:', '^<F-NOFAIL><F-MLFFORGET>(Connection closed|Disconnected)</F-MLFFORGET></F-NOFAIL> (?:by|from)(?: (?:invalid|authenticating) user <F-USER>\\S+|.*?</F-USER>)? <HOST>(?:(?: (?:port \\d+|on \\S+|\\[preauth\\])){0,3}\\s*|\\s*)$', '^<F-MLFFORGET><F-MLFGAINED>Accepted \\w+</F-MLFGAINED></F-MLFFORGET> for <F-USER>\\S+</F-USER> from <HOST>(?:\\s|$)', '^<F-NOFAIL>Connection from</F-NOFAIL> <HOST>']], ['set', 'sshd', 'datepattern', '{^LN-BEG}'], ['set', 'sshd', 'addjournalmatch', '_SYSTEMD_UNIT=sshd.service', '+', '_COMM=sshd'], ['set', 'sshd', 'maxretry', 5], ['set', 'sshd', 'maxmatches', 5], ['set', 'sshd', 'findtime', '10m'], ['set', 'sshd', 'bantime', '10m'], ['set', 'sshd', 'ignorecommand', ''], ['set', 'sshd', 'logencoding', 'auto'], ['set', 'sshd', 'addaction', 'iptables-multiport'], ['multi-set', 'sshd', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-sshd\n<iptables> -A f2b-sshd -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports ssh -j f2b-sshd'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports ssh -j f2b-sshd\n<iptables> -F f2b-sshd\n<iptables> -X f2b-sshd'], ['actionflush', '<iptables> -F f2b-sshd'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-sshd[ \\t]'"], ['actionban', '<iptables> -I f2b-sshd 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-sshd -s <ip> -j <blocktype>'], ['port', 'ssh'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'sshd'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['add', 'keyhelp-postfix', 'systemd'], ['set', 'keyhelp-postfix', 'usedns', 'warn'], ['set', 'keyhelp-postfix', 'prefregex', '^\\s*(?:\\S+\\s+)?(?:postfix(-\\w+)?/\\w+(?:/smtp[ds])?(?:\\[\\d+\\])?:?\\s+)?(?:kernel:\\s?\\[ *\\d+\\.\\d+\\]:?\\s+)?(?:\\w+: reject:|(?:improper command pipelining|too many errors) after \\S+) <F-CONTENT>.+</F-CONTENT>$'], ['multi-set', 'keyhelp-postfix', 'addfailregex', ['^RCPT from [^[]*\\[<HOST>\\](?::\\d+)?: 55[04] 5\\.7\\.1\\s', '^RCPT from [^[]*\\[<HOST>\\](?::\\d+)?: 45[04] 4\\.7\\.\\d+ (?:Service unavailable\\b|Client host rejected: cannot find your (reverse )?hostname\\b)', '^RCPT from [^[]*\\[<HOST>\\](?::\\d+)?: 450 4\\.7\\.\\d+ (<[^>]*>)?: Helo command rejected: Host not found\\b', '^EHLO from [^[]*\\[<HOST>\\](?::\\d+)?: 504 5\\.5\\.\\d+ (<[^>]*>)?: Helo command rejected: need fully-qualified hostname\\b', '^(RCPT|VRFY) from [^[]*\\[<HOST>\\](?::\\d+)?: 550 5\\.1\\.1\\s', '^RCPT from [^[]*\\[<HOST>\\](?::\\d+)?: 450 4\\.1\\.\\d+ (<[^>]*>)?: Sender address rejected: Domain not found\\b', '^from [^[]*\\[<HOST>\\](?::\\d+)?:?']], ['set', 'keyhelp-postfix', 'datepattern', '{^LN-BEG}'], ['set', 'keyhelp-postfix', 'addjournalmatch', '_SYSTEMD_UNIT=postfix.service'], ['set', 'keyhelp-postfix', 'maxretry', 6], ['set', 'keyhelp-postfix', 'maxmatches', 6], ['set', 'keyhelp-postfix', 'findtime', '10m'], ['set', 'keyhelp-postfix', 'bantime', '10m'], ['set', 'keyhelp-postfix', 'ignorecommand', ''], ['set', 'keyhelp-postfix', 'logencoding', 'auto'], ['set', 'keyhelp-postfix', 'addaction', 'iptables-multiport'], ['multi-set', 'keyhelp-postfix', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-keyhelp-postfix\n<iptables> -A f2b-keyhelp-postfix -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports smtp,ssmtp,smtps,submission,submissions -j f2b-keyhelp-postfix'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports smtp,ssmtp,smtps,submission,submissions -j f2b-keyhelp-postfix\n<iptables> -F f2b-keyhelp-postfix\n<iptables> -X f2b-keyhelp-postfix'], ['actionflush', '<iptables> -F f2b-keyhelp-postfix'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-keyhelp-postfix[ \\t]'"], ['actionban', '<iptables> -I f2b-keyhelp-postfix 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-keyhelp-postfix -s <ip> -j <blocktype>'], ['port', 'smtp,ssmtp,smtps,submission,submissions'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'keyhelp-postfix'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['add', 'keyhelp-dovecot', 'systemd'], ['set', 'keyhelp-dovecot', 'usedns', 'warn'], ['set', 'keyhelp-dovecot', 'prefregex', '^\\s*(?:\\S+\\s+)?(?:(?:dovecot(?:-auth)?|auth)(?:\\[\\d+\\])?:?\\s+)?(?:kernel:\\s?\\[ *\\d+\\.\\d+\\]:?\\s+)?(?:(?:dovecot: )?auth(?:-worker)?(?:\\([^\\)]+\\))?: )?(?:pam_unix(?:\\(dovecot:auth\\))?: |(?:pop3|imap|managesieve|submission)-login: )?(?:Info: )?<F-CONTENT>.+</F-CONTENT>$'], ['multi-set', 'keyhelp-dovecot', 'addfailregex', ['^authentication failure; logname=<F-ALT_USER1>\\S*</F-ALT_USER1> uid=\\S* euid=\\S* tty=dovecot ruser=<F-USER>\\S*</F-USER> rhost=<HOST>(?:\\s+user=<F-ALT_USER>\\S*</F-ALT_USER>)?\\s*$', '^(?:Aborted login|Disconnected|Remote closed connection|Client has quit the connection)(?::(?: [^ \\(]+)+)? \\((?:auth failed, \\d+ attempts(?: in \\d+ secs)?|tried to use (?:disabled|disallowed) \\S+ auth|proxy dest auth failed)\\):(?: user=<<F-USER>[^>]*</F-USER>>,)?(?: method=\\S+,)? rip=<HOST>(?:[^>]*(?:, session=<\\S+>)?)\\s*$', '^pam\\(\\S+,<HOST>(?:,\\S*)?\\): pam_authenticate\\(\\) failed: (?:User not known to the underlying authentication module: \\d+ Time\\(s\\)|Authentication failure \\(password mismatch\\?\\)|Permission denied)\\s*$', '^[a-z\\-]{3,15}\\(\\S*,<HOST>(?:,\\S*)?\\): (?:unknown user|invalid credentials|Password mismatch)']], ['set', 'keyhelp-dovecot', 'datepattern', '{^LN-BEG}TAI64N\n{^LN-BEG}'], ['set', 'keyhelp-dovecot', 'addjournalmatch', '_SYSTEMD_UNIT=dovecot.service'], ['set', 'keyhelp-dovecot', 'maxretry', 10], ['set', 'keyhelp-dovecot', 'maxmatches', 10], ['set', 'keyhelp-dovecot', 'findtime', '10m'], ['set', 'keyhelp-dovecot', 'bantime', '10m'], ['set', 'keyhelp-dovecot', 'ignorecommand', ''], ['set', 'keyhelp-dovecot', 'logencoding', 'auto'], ['set', 'keyhelp-dovecot', 'addaction', 'iptables-multiport'], ['multi-set', 'keyhelp-dovecot', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-keyhelp-dovecot\n<iptables> -A f2b-keyhelp-dovecot -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports pop3,pop3s,imap,imaps,submission,submissions,sieve -j f2b-keyhelp-dovecot'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports pop3,pop3s,imap,imaps,submission,submissions,sieve -j f2b-keyhelp-dovecot\n<iptables> -F f2b-keyhelp-dovecot\n<iptables> -X f2b-keyhelp-dovecot'], ['actionflush', '<iptables> -F f2b-keyhelp-dovecot'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-keyhelp-dovecot[ \\t]'"], ['actionban', '<iptables> -I f2b-keyhelp-dovecot 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-keyhelp-dovecot -s <ip> -j <blocktype>'], ['port', 'pop3,pop3s,imap,imaps,submission,submissions,sieve'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'keyhelp-dovecot'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['add', 'keyhelp-proftpd', 'systemd'], ['set', 'keyhelp-proftpd', 'usedns', 'warn'], ['set', 'keyhelp-proftpd', 'prefregex', '^\\s*(?:\\S+\\s+)?(?:proftpd(?:\\[\\d+\\])?:?\\s+)?(?:kernel:\\s?\\[ *\\d+\\.\\d+\\]:?\\s+)?\\S+ \\(\\S+\\[<HOST>\\]\\)[: -]+ <F-CONTENT>(?:USER|SECURITY|Maximum) .+</F-CONTENT>$'], ['multi-set', 'keyhelp-proftpd', 'addfailregex', ["^USER <F-USER>\\S+|.*?</F-USER>(?: \\(Login failed\\))?: ([uU]ser not authorized for login|[nN]o such user found|[iI]ncorrect password|[pP]assword expired|[aA]ccount disabled|[iI]nvalid shell: '\\S+'|[uU]ser in \\S+|[lL]imit (access|configuration) denies login|[nN]ot a UserAlias|[mM]aximum login length exceeded)", '^SECURITY VIOLATION: <F-USER>\\S+|.*?</F-USER> login attempted', '^Maximum login attempts \\(\\d+\\) exceeded']], ['set', 'keyhelp-proftpd', 'datepattern', '{^LN-BEG}'], ['set', 'keyhelp-proftpd', 'addjournalmatch', '_SYSTEMD_UNIT=proftpd.service'], ['set', 'keyhelp-proftpd', 'maxretry', 6], ['set', 'keyhelp-proftpd', 'maxmatches', 6], ['set', 'keyhelp-proftpd', 'findtime', '10m'], ['set', 'keyhelp-proftpd', 'bantime', '10m'], ['set', 'keyhelp-proftpd', 'ignorecommand', ''], ['set', 'keyhelp-proftpd', 'logencoding', 'auto'], ['set', 'keyhelp-proftpd', 'addaction', 'iptables-multiport'], ['multi-set', 'keyhelp-proftpd', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-keyhelp-proftpd\n<iptables> -A f2b-keyhelp-proftpd -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports ftp,ftp-data,ftps,ftps-data -j f2b-keyhelp-proftpd'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports ftp,ftp-data,ftps,ftps-data -j f2b-keyhelp-proftpd\n<iptables> -F f2b-keyhelp-proftpd\n<iptables> -X f2b-keyhelp-proftpd'], ['actionflush', '<iptables> -F f2b-keyhelp-proftpd'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-keyhelp-proftpd[ \\t]'"], ['actionban', '<iptables> -I f2b-keyhelp-proftpd 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-keyhelp-proftpd -s <ip> -j <blocktype>'], ['port', 'ftp,ftp-data,ftps,ftps-data'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'keyhelp-proftpd'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['add', 'keyhelp-phpmyadmin', 'systemd[journalflags=1]'], ['set', 'keyhelp-phpmyadmin', 'usedns', 'warn'], ['multi-set', 'keyhelp-phpmyadmin', 'addfailregex', ['^.* phpMyAdmin\\[.*\\]: user denied: .* \\((mysql-denied|allow-denied|root-denied|empty-denied)\\) from <HOST>$', '^.* phpMyAdmin\\[.*\\]: message repeated \\d* times: \\[ user denied: .* \\((mysql-denied|allow-denied|root-denied|empty-denied)\\) from <HOST>\\]$']], ['set', 'keyhelp-phpmyadmin', 'addjournalmatch', 'SYSLOG_IDENTIFIER=phpMyAdmin'], ['set', 'keyhelp-phpmyadmin', 'maxretry', 6], ['set', 'keyhelp-phpmyadmin', 'maxmatches', 6], ['set', 'keyhelp-phpmyadmin', 'findtime', '10m'], ['set', 'keyhelp-phpmyadmin', 'bantime', '10m'], ['set', 'keyhelp-phpmyadmin', 'ignorecommand', ''], ['set', 'keyhelp-phpmyadmin', 'logencoding', 'auto'], ['set', 'keyhelp-phpmyadmin', 'addaction', 'iptables-multiport'], ['multi-set', 'keyhelp-phpmyadmin', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-keyhelp-phpmyadmin\n<iptables> -A f2b-keyhelp-phpmyadmin -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports http,https -j f2b-keyhelp-phpmyadmin'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports http,https -j f2b-keyhelp-phpmyadmin\n<iptables> -F f2b-keyhelp-phpmyadmin\n<iptables> -X f2b-keyhelp-phpmyadmin'], ['actionflush', '<iptables> -F f2b-keyhelp-phpmyadmin'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-keyhelp-phpmyadmin[ \\t]'"], ['actionban', '<iptables> -I f2b-keyhelp-phpmyadmin 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-keyhelp-phpmyadmin -s <ip> -j <blocktype>'], ['port', 'http,https'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'keyhelp-phpmyadmin'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['add', 'keyhelp-roundcube', 'systemd[journalflags=1]'], ['set', 'keyhelp-roundcube', 'usedns', 'warn'], ['set', 'keyhelp-roundcube', 'prefregex', '^\\s*(\\[\\])?(\\S+\\s*(?:roundcube(?:\\[(\\d*)\\])?:)?\\s*(<[\\w]+>)? IMAP Error)?: <F-CONTENT>.+</F-CONTENT>$'], ['set', 'keyhelp-roundcube', 'addignoreregex', 'Could not connect to .* Connection refused'], ['multi-set', 'keyhelp-roundcube', 'addfailregex', ['^(?:FAILED login|Login failed) for <F-USER>.*</F-USER> from <HOST>(?:(?:\\([^\\)]*\\))?\\. (?:(?! from ).)*(?: user=(?P=user))? in \\S+\\.php on line \\d+ \\(\\S+ \\S+\\))?$', '^(?:<[\\w]+> )?Failed login for <F-USER>.*</F-USER> from <HOST> in session \\w+( \\(error: \\d\\))?$']], ['set', 'keyhelp-roundcube', 'datepattern', '{^LN-BEG}'], ['set', 'keyhelp-roundcube', 'addjournalmatch', 'SYSLOG_IDENTIFIER=roundcube'], ['set', 'keyhelp-roundcube', 'maxretry', 10], ['set', 'keyhelp-roundcube', 'maxmatches', 10], ['set', 'keyhelp-roundcube', 'findtime', '10m'], ['set', 'keyhelp-roundcube', 'bantime', '10m'], ['set', 'keyhelp-roundcube', 'ignorecommand', ''], ['set', 'keyhelp-roundcube', 'logencoding', 'auto'], ['set', 'keyhelp-roundcube', 'addaction', 'iptables-multiport'], ['multi-set', 'keyhelp-roundcube', 'action', 'iptables-multiport', [['actionstart', '<iptables> -N f2b-keyhelp-roundcube\n<iptables> -A f2b-keyhelp-roundcube -j RETURN\n<iptables> -I INPUT -p tcp -m multiport --dports http,https -j f2b-keyhelp-roundcube'], ['actionstop', '<iptables> -D INPUT -p tcp -m multiport --dports http,https -j f2b-keyhelp-roundcube\n<iptables> -F f2b-keyhelp-roundcube\n<iptables> -X f2b-keyhelp-roundcube'], ['actionflush', '<iptables> -F f2b-keyhelp-roundcube'], ['actioncheck', "<iptables> -n -L INPUT | grep -q 'f2b-keyhelp-roundcube[ \\t]'"], ['actionban', '<iptables> -I f2b-keyhelp-roundcube 1 -s <ip> -j <blocktype>'], ['actionunban', '<iptables> -D f2b-keyhelp-roundcube -s <ip> -j <blocktype>'], ['port', 'http,https'], ['protocol', 'tcp'], ['chain', '<known/chain>'], ['name', 'keyhelp-roundcube'], ['actname', 'iptables-multiport'], ['blocktype', 'REJECT --reject-with icmp-port-unreachable'], ['returntype', 'RETURN'], ['lockingopt', '-w'], ['iptables', 'iptables <lockingopt>'], ['blocktype?family=inet6', 'REJECT --reject-with icmp6-port-unreachable'], ['iptables?family=inet6', 'ip6tables <lockingopt>']]], ['start', 'sshd'], ['start', 'keyhelp-postfix'], ['start', 'keyhelp-dovecot'], ['start', 'keyhelp-proftpd'], ['start', 'keyhelp-phpmyadmin'], ['start', 'keyhelp-roundcube']]] has failed. Received RuntimeError("Failed to initialize any backend for Jail 'sshd'")
2024-01-22 13:52:48,156 fail2ban [146293]: ERROR NOK: ("Failed to initialize any backend for Jail 'sshd'",)